Mastering Buffer Overflow: Unlocking the Secrets to Secure Software Development
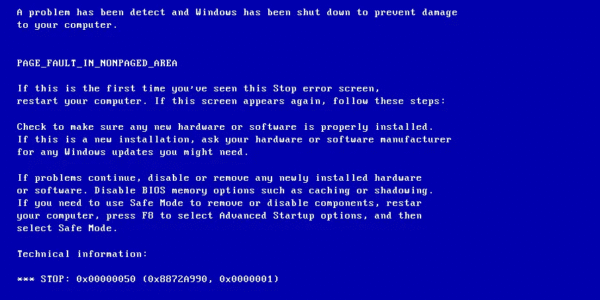
Buffer overflow is one of the most notorious vulnerabilities in the world of cybersecurity, and it has been responsible for many high-profile security breaches. Understanding how buffer overflow works, its potential risks, and how to prevent it is essential for…
Understanding Memory Corruption: Causes, Impact, and Protection
Memory corruption is a serious vulnerability in software and hardware systems that can have devastating consequences. It occurs when data in a program’s memory is unintentionally modified, which can lead to unpredictable behavior, crashes, security flaws, and even complete system…
What Are Zero-Day Vulnerabilities? Everything You Need to Know
What Are Zero-Day Vulnerabilities? In today’s fast-paced cybersecurity landscape, zero-day vulnerabilities are some of the most dangerous threats organizations face. These flaws are exploited before developers even know they exist—making them incredibly hard to detect and defend against. If you’re…